Conquering the Digital World with Zero Trust!
- Farhan
- Jun 5, 2024
- 4 min read
Updated: Jun 7, 2024
Welcome to PowerUp Cyber, your ultimate destination for fortifying your digital defenses! Today, we're unveiling a potent weapon in your cybersecurity arsenal: Zero Trust.

Imagine an impregnable shield safeguarding your digital kingdom from cunning cyber villains. Forget the days of wide-open gates. Zero Trust operates on a "never trust, always verify" principle – like a watchful castle guard meticulously checking every adventurer entering your kingdom.
The Quest: Why Power Up with Zero Trust?
Traditional cybersecurity models relied on a trust-based system, similar to a single massive entrance to your kingdom. Anyone with the "correct" sigil could enter. But what if a malicious goblin stole a sigil or even forged their own? Disaster strikes!
This is the inherent weakness of traditional security. Hackers can exploit stolen credentials or weak access points to wreak havoc. Zero trust tackles this head-on by constantly verifying everyone and everything.
Building Your Defenses: The Core Elements of Zero Trust
Zero trust is a multi-layered defense system, much like a legendary suit of armor. Here are some key concepts we'll explore:
Limited File Permissions: Instead of a single key unlocking the entire castle, imagine specific keys for each treasure room. Zero trust restricts access to specific files and folders, ensuring only authorized heroes (aka users) can access confidential information.
Least Privilege Access: Think of assigning roles within your guild. A potion maker doesn't need access to the royal armory! Zero trust grants only the minimum permissions users need for their tasks. This way, even if a villain breaches a single area, they won't have access to everything!
Gear Up for Zero Trust!
To conquer the digital world with zero trust, you'll need to assemble a formidable arsenal:
A Powerful Web Server: This acts as the central hub of your kingdom, where your valuable information (treasure) resides. We'll be using a free and user-friendly option called XAMPP for this demonstration. XAMPP is a free and open-source cross-platform web server solution stack package developed by Apache Friends XAMPP is often used for local development and testing purposes, providing a convenient way to set up a complete web server environment on a personal computer without having to install each component separately. You can download it from here: https://www.apachefriends.org/
A Reliable Text Editor: Think of this as your trusty sword for crafting access control rules. We recommend using a free, versatile option like Notepad++ that allows you to save your files in different formats, including .html. You can download it from here: https://notepad-plus-plus.org/
Basic Knowledge of File Permissions: Imagine assigning keys to specific castle chambers. Understanding file permissions allows you to control who can access what information on your website.
Putting it into Practice: A Zero-Trust Demo
We built a simple simulation to demonstrate zero trust principles on a Windows machine. The same concepts can be applied on Mac or Linux OS accordingly.
Scenario: Simulating Access Control with Limited Permissions
Steps
Download and Install XAMPP:
Download the latest version of XAMPP for Windows from the official website.
Run the installer and follow the on-screen instructions, choosing the "Basic" installation.
Create a Simple Website:
Open the XAMPP Control Panel and start the "Apache" and "MySQL" modules if they're not running already.
Navigate to the "htdocs" folder within your XAMPP installation directory (e.g., C:\xampp\htdocs).
Create a new folder named "restricted" and a text file named "index.html" inside it.
Build the Restricted Website (index.html): Open the "index.html" file in a text editor like Notepad++ (recommended for various file formats). Use the following basic HTML code:
Explanation: This code creates a simple webpage indicating it's a restricted area.
Simulate User Access Control:
Now, the interesting part! By default, anyone on your network can access this website by going to http://localhost/restricted/ in their web browser
This represents unrestricted access, which goes against zero-trust principles.
Simulate Limited Permissions:
To showcase zero-trust, we'll restrict access to a specific folder within the website.
Create a file named "secret.txt" inside the "htdocs/restricted" folder path.
Configure Apache Access Restriction (.htaccess):
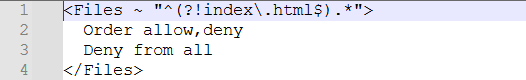
Create a new file named ".htaccess" (note the leading dot) inside the "restricted" folder (the same level as "index.html").
Open ".htaccess" in a text editor and add the following line and save your file:
Test Restricted Access:
Now, if you try to access http://localhost/restricted/secret.txt in your web browser, you'll be denied access. The ".htaccess" file with the "Deny from all" rule restricts access to anything within the "htdocs" folder except the "index.html" file we created earlier.
Explanation: This demonstrates a basic concept of zero-trust: By default, no access is granted (deny all), and specific permissions are required to access resources (like allowing access only to the "index.html" file - see screenshot below):
Limitations:
In case the .htaccess file rules are not taking precedence, you can use a more simpler option by limiting access with file permissions. By right clicking on the secret.txt file, you can set the deny access to a specified group or individual. In windows, right click on the file and navigate to the security tab, check the deny options for the specified user or group. Also, you can checkout troubleshooting tips from XAMPP's official site.
This is a simplified example. Real-world zero-trust involves more sophisticated authentication and authorization mechanisms.
XAMPP offers basic security features. For a more robust implementation, consider dedicated web server software.
Key Takeaway: This demo is easy to set up with free, open-source tools on your Windows machine. It effectively showcases the core principle of "least privilege" in zero-trust, where users only have the minimum access necessary for their tasks. Remember, this is for educational purposes only. Always ensure proper security practices when deploying web servers or implementing access control mechanisms in real-world environments.
Until next time, PowerUp, my fellow cyber gamers! Subscribe to my site and follow my channels for more tips and content!



Comentários